Summary
WANSecurity's VPN access controller solution is built on OpenBSD enabling site-to-site VPN, and road-warrior dial-up VPN Access. Telecommute safely using the VPN clients already built into your operating system. This provides an extremely cost-effective solution to secure remote access for telecommuters. In addition to robust VPN support, these devices are home to some of the best firewalling code on the planet namely OpenBSD's PF, and Linux IPFilter. In addition to being a powerful, flexible VPN, firewalling, routing platform, it includes a long list of related features.
Feature
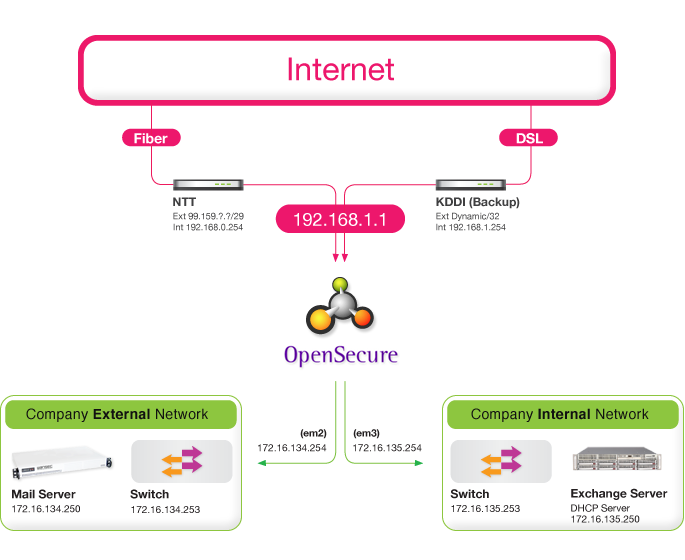
Supports a wide variety of network operational support and functionality.
- low-cost, high-quality alternative
- IPSec
- IPComp
- IPsec-encapsulated ethernet bridging
- high speed data transfer support
- jumbo frame support
- 802.1Q VLAN Tagging and Interfaces
- highly extensible Packet Filter
- Queuing
- NAT
- Layers 3-7 Redundancy
- Load balancing
- Layer7 Load Balancing
- 802.11 access point mode
- Real-time Failover and State Synchronization
Routing and other Protocol Support
- BGP
- OSPF
- RIP
- SNMP
- DVMRP
- IPv6
- Netflow
IPSEC
IPsec allows connectivity with any device supporting standard IPsec. This is most commonly used for site to site connectivity to other VPNAC installations, other open source firewalls, FreeBSD, OpenBSD, Linux and most all commercial firewall solutions (Cisco, Juniper, etc.). It can also be used for mobile client connectivity.
PPTP
PPTP is a popular VPN option because nearly every OS has a built in PPTP client, including every Windows release since Windows 95 OSR2.The PPTP Server can use a local user database, or a RADIUS server for authentication. RADIUS accounting is also supported. Firewall rules on the PPTP interface control traffic initiated by PPTP clients.
- Microsoft compatible authentication and encryption
(MSCHAPv2, MPPE 40 - 128 bit RC4 encryption) - Support for hundreds of simultaneous client connections
- Seamless integration into a Microsoft network environment (LDAP, SAMBA) using RADIUS
- Support for Windows 95/98/Me/NT/2000/XP/Vista PPTP clients
- Support for Linux and OSX Panther, Tiger, and Leopard PPTP clients
- Based on Open Source Software
Authentication
VPNAC supports both local authentication, and authentication via RADIUS enabling authentication against Microsoft Active Directory, or LDAP.
- Seamless integration into a Microsoft network environment (LDAP, SAMBA) using RADIUS
Firewall
Packet Filter aka PF is OpenBSD's system for filtering TCP/IP traffic and doing Network Address Translation. PF is also capable of normalizing and conditioning TCP/IP traffic and providing bandwidth control and packet prioritization. PF is the most advanced firewall available on the planet.
- Filter by Computer Operating System
- Logging on a per rule basis
- Highly flexible policy routing, allowing multiple gateways
- Aliases, Grouping, and Naming of IP Pools, Networks, and Interfaces
- Packet Normalization removes ambiguities in packet reassembly
- True Stateful Packet Inspection aka SPI
Failover
CARP from OpenBSD allows for hardware failover. Two or more VPNAC devices can be configured as a failover group. If one interface fails on the primary or the primary goes offline entirely, the secondary becomes active. VPNAC also includes configuration synchronization capabilities, so you make your configuration changes on the primary and they automatically synchronize to the secondary firewall.VPNAC ensures the firewall's state table is replicated to all failover configured firewalls. This means your existing connections will be maintained in the case of failure, which is important to prevent network disruptions.
Load Balancing
Inbound
Inbound load balancing is used to distribute load between multiple servers. This is commonly used with web servers, mail servers, and others. Servers that fail to respond to ping requests or TCP port connections are removed from the pool.
- Equally distributes load between all available servers
- Ping checks ensure forwarding servers are alive and active
Outbound
Outbound load balancing can be acheived via the use of multi homed routing. load balancing and failover capabilities. Traffic is directed to the desired gateway or load balancing pool on a per-firewall rule basis.
